USE CASE
Modernising Legacy IAM
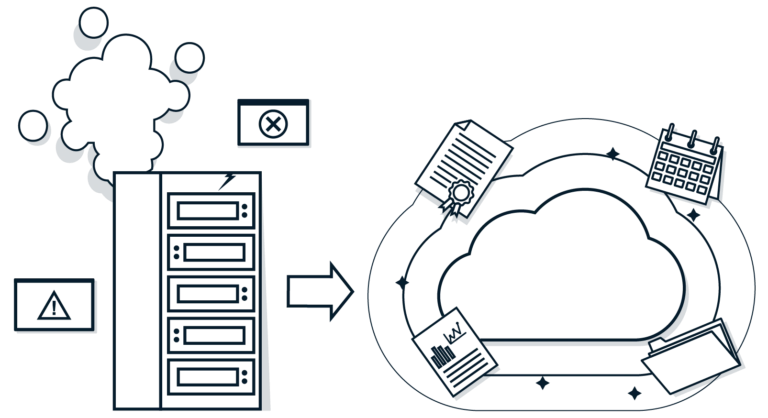
Achieve controlled growth from a legacy Authentication & Authorisation system to a modern role-based account and rights management system with our Identity-as-a-Service solution.
CHALLENGE
How Do You Prepare Your IAM Environment for the Upcoming Challenges?
Many existing IAM solutions are costly to maintain, limited in functionality, far from user-friendly and not future-proof. They were once developed for efficient but limited access management, but these days we need much more from a modern IAM in order to align with the rapidly evolving digitalisation and the increasingly stringent privacy and information security guidelines.
NECESSITIES
Features
HOW IT WORKS
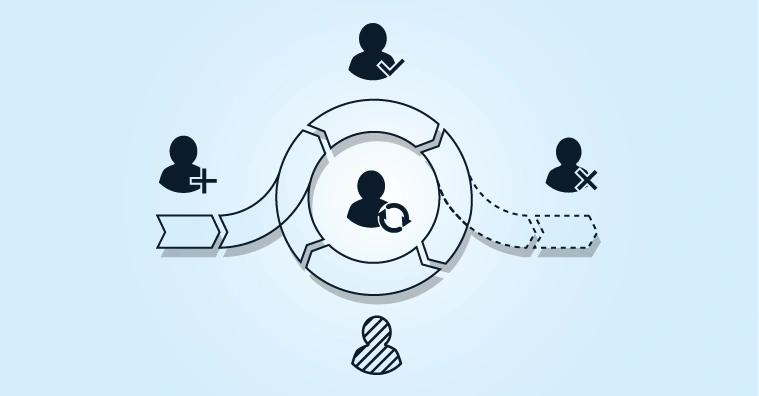
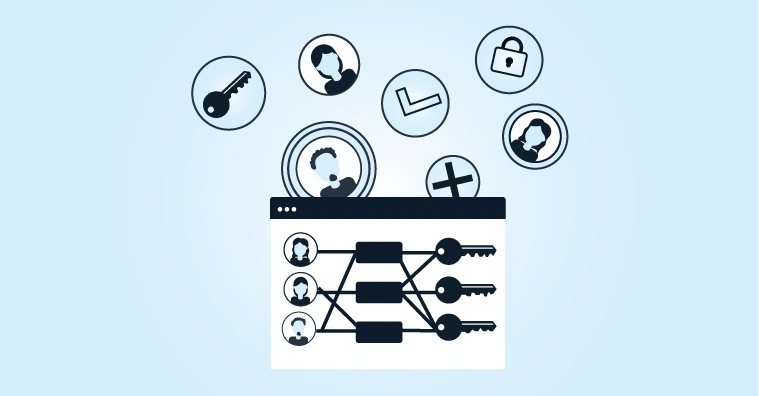
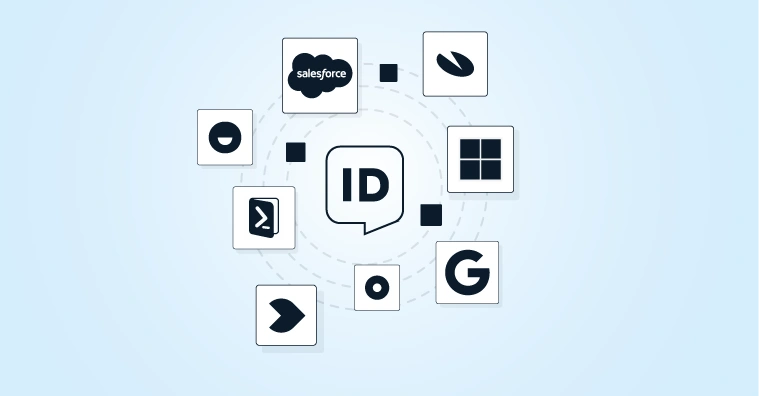
How We Migrate From a Legacy IAM System to the HelloID IDaaS Solution
7 steps that can each be configured using low-code or no-code solutions
Source system: Integration of HelloID with source systems such as HR, SIS and/or scheduling systems. This way, changes in the source data are automatically available in HelloID.
People: Conversion of data about people/roles from source systems to a common representation within HelloID using an ‘identity vault’.
Business rules: Determining rules that determine which roles are granted which types of accounts and access rights, and under what conditions.
Target systems: Linking HelloID to on-premises and/or cloud-based applications. This can be executed step by step per application.
Service processes: Automating processes, including online approval flows and activation in target systems. This can be carried out step by step for each process.
Access management: Set up access procedures, such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA), in conjunction with — for example — Active Directory.
Reporting and auditing: Configuring standard and client-specific reports and monitoring functions for analysis and audits.