
Role mining
In this article
- What is role mining?
- Why role mining?
- Access based on roles
- Role mining for the composition of business rules
- How does the role mining process work?
- Types of role mining: bottom-up and top-down?
- Can I manage all access rights based on roles?
- Service Automation for optional access rights
- 5 role mining tips
- Role mining best practices and more information
What is role mining?
Role mining enables you to map out all relevant user roles and their access rights in an iterative way. The input from a role mining project provides you with the necessary data to implement Role Based Access Control (RBAC) in an organisation. We explain our role mining approach in the article below.
Why role mining?
With such a role-based authorisation mechanism, you assign accounts and access rights based on someone’s department, job, or role[1] within the organisation. For instance, if you work in the finance department, you would have access not only to a standard Outlook and Office account but also to the financial systems. If you move to a new role within the sales team, your finance access rights are automatically revoked, and you are granted access to the CRM system and associated customer data instead.
Access based on roles
This ensures that everyone has the access rights necessary for their role, known as ‘birthright’ access. Since this happens automatically, it prevents people from accumulating unnecessary rights. Thus, you make your access management more efficient and improve your information security and compliance.
The basis for this is a structured overview in which all roles in your organisation are recorded, and for each role, all necessary applications and access rights. How you implement and manage such a structure of roles and associated rights depends on the Identity and Access Management (IAM) platform used. Sometimes, what is known as an authorisation matrix is implemented; within HelloID, we use so-called business rules for this purpose. In such a business rule, you could specify, for example, that someone with the role of ‘financial employee’ always has access to the financial system.
A major advantage of business rules over regular RBAC is that we are not limited to roles alone. You can also use various other characteristics (also known as ‘attributes’) and process rules to determine someone’s access rights. For example, you can include a rule that accounts for new employees are activated exactly one day before onboarding. Therefore, business rules offer more flexibility and possibilities. Essentially, with HelloID, you are talking about ABAC (Attribute Based Access Control).
Role mining for the composition of business rules
But how can you compose such business rules? You can, of course, start from scratch with a complete business analysis. In this, you would map all functions and processes, including the applications and data needed. However, this is a complex and lengthy trajectory.
A more accessible approach is to start with a role mining analysis. Role mining makes as much reuse of existing knowledge as possible. After all, even before you apply role-based authorisation, you already have to provide accounts and access rights to your users. And even then, you try to take into account someone’s role and duties as much as possible. By now collecting all account(s), access rights, and group settings from existing users in your IT systems and thoroughly analysing this data, you can quickly create a first version of your set of business rules. This initial set of rules can then be refined progressively. With such a pragmatic role mining approach, you avoid a long, complicated business analysis.
How does the role mining process work?
For this iterative role mining process, Tools4ever uses its own role mining scan tool. We follow the next steps with our clients:
- Inventory of existing roles: We collect the various roles as registered for employees within the HR system.
- Inventory of existing rights and/or groups: We gather from IT sources such as Entra ID or Active Directory the currently actually assigned authorisations and user groups.
- Role-based authorisation design: We match the information from the previous two steps, analyse and distil patterns from it, and create an initial concept of roles and associated rights.
- Concept evaluation: With stakeholders such as department managers, we look for inaccuracies. We also look for contamination, for example, by the accumulation of previous rights. We adjust the concept accordingly.
- First baseline for a role-based authorisation model: This baseline can already be operational and can also be continuously expanded, refined, and updated based on new insights.
The role mining process is thus iterative, hands-on, and pragmatic. You start with your existing users and their access rights as you currently have them in use within your IT environment. You can map all relevant roles and associated rights with our role mining scan, together with a team from the organisation. We can then configure this in the form of business rules in the HelloID environment.
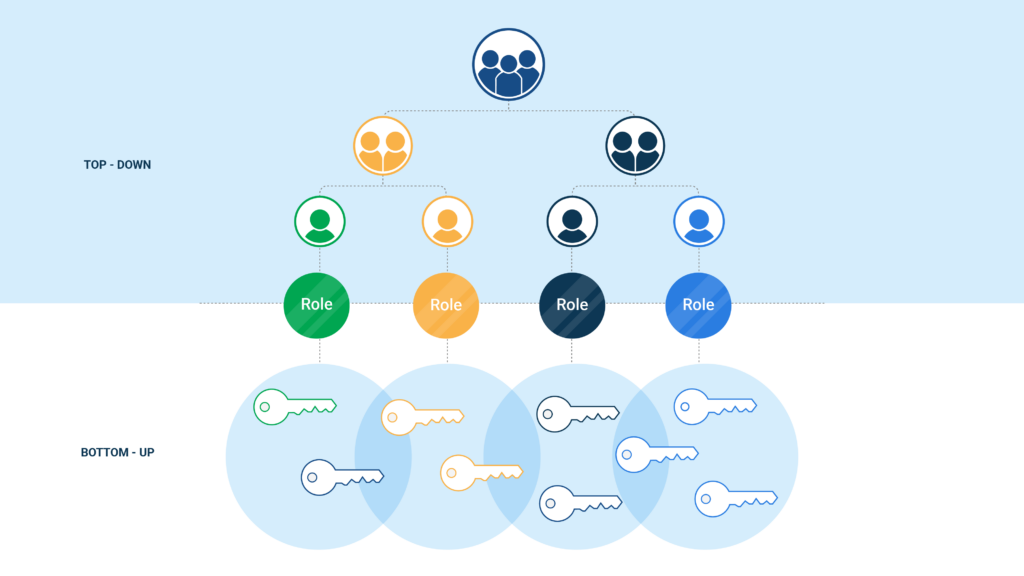
Types of role mining: bottom-up and top-down?
You sometimes come across the terms bottom-up or top-down role mining. These are two different approaches:
- Top-down role mining: In modern HR systems, personal information as well as agreements about an employee’s department(s), job(s), and/or role(s) are registered. This provides a source with all the roles used in an organisation.
- Bottom-up role mining: You can gather currently actually granted access rights, users, and user groups from existing applications and IT systems – such as Active Directory or Entra ID.
What is special about the Tools4ever role mining approach is that we optimally combine these approaches. The top-down and bottom-up analyses together form steps 1 & 2 of the Tools4ever role mining process that we described in the paragraph above. By analysing and matching the top-down and bottom-up data, you can quickly and effectively develop and refine an initial roles-rights model.
Can I manage all access rights based on roles?
Role mining is thus a tool to implement role-based authorisation. At the same time, such a role-based authorisation also has its limitations. For sharply defined roles – such as an administrator – you can usually manage the access rights simply based on someone’s role. Such roles are also referred to as key roles. However, there are also roles where this alone is not sufficient. We give two examples:
- For less strictly defined roles such as a project manager or IT developer, the required rights usually depend on their specific project(s). Just their role then says insufficient. For one assignment, someone might need a Visio account, while for another project, they must use MS Project.
- But even for well-defined roles, there are exceptions. Many people have additional tasks alongside their standard duties or, for example, temporarily participate in a project. Or they are also active as a first aider or union representative. All these are reasons why you might sometimes need extra access rights.
If you were to include all these exceptions role-based, you would gradually start to define more and more different roles. So instead of one administrator role, you soon have multiple variants. Or users are assigned extra roles for various side tasks (the role OR member). As soon as you realise during your role mining analysis that you are defining roles that apply to only one or a few users, we overshoot our goal.
Service Automation for optional access rights
That means that in addition to a role-based approach, you also need a solution to issue and manage optional access rights – the exceptions. For this, HelloID has a Service Automation Module. With it, you can set up a self-service portal where employees or their managers can request application or access rights themselves. You can easily add steps for online approval of such a request by the responsible manager(s) with HelloID. You can also automatically limit the validity duration of such access rights to prevent unnecessary accumulation of rights.
Effective account and rights management thus requires seamless cooperation between Role Based Access Control (assembled with the help of role mining) and service automation for all optional access rights.
5 role mining tips
In a role mining project, there are several points of attention:
- With role mining, the key is not to make it a theoretical analysis. From the first employee, an organisation starts issuing accounts and access rights. Use that knowledge and experience to make your first blueprint of roles and rights as simple as possible.
- Work top-down and bottom-up. It’s about matching the knowledge of the employees and their formal roles (registered in the HR systems) with the actually granted access rights within your IT environment.
- In role mining, your data is almost always contaminated. Until the implementation of RBAC, rights management is usually (semi) manual. As a result, many users have gradually accumulated more and more access rights, and mistakes have been made. Cleaning up data is thus an important part of role mining.
- Data mining is an iterative process. You create a concept based on your data. You then check, discuss, and improve that concept. This way, you can continuously expand, refine, and update your role-based model. It’s also wise to repeat your role mining regularly – for example, biannually – not like the first time for the design but to map out deltas and errors.
- Not everything can be processed in a role-based model; optional rights remain necessary. With an IAM solution like HelloID, you can seamlessly integrate your role-based authorisation with your further account management processes.
Role mining best practices and more information
With role mining, we thus combine HR data and data from IT systems to quickly and efficiently develop and implement an initial structure of roles and rights. For this, we use our HelloID role mining tools. After the technical extraction of the data, analysis, verification, and consultation are necessary to develop an initial baseline. Points of attention include removing existing errors, contamination, and unnecessary accumulation of access rights. Tools4ever business consultants have extensive experience with this and assist you in a clear, defined consultancy trajectory. Through the role mining webinar, you get an introduction to this method, which has been applied at numerous clients to quickly make a baseline set of business rules.
[1] From now on, we mainly use the term ‘role’, but in practice, it can also involve functions and departments.