
Identity life cycle
Just like your identity in real life, your digital identities and accounts also go through a specific life cycle. Your digital identity can vary depending on the process or system. And as your role, position or status within an organisation changes, your digital identities and accounts change with it. This is how an identity life cycle is established. But what exactly do we mean by this term? And how do you manage an identity life cycle?
What is an identity life cycle?
The identity life cycle refers to the various phases of the existence of a digital identity or user account, from the moment it is created until the moment it is deleted. The life cycle of the identity includes all steps of managing a user's identity, including the processes of creation, activation, flow-through, deactivation and removal.
Wat is identity life cycle management?
Identity life cycle management is a crucial part of IAM and ensures a streamlined and secure way to manage user accounts. By effectively managing the identity life cycle, organisations can ensure that the right people have access to the right information at the right times, and they can also minimise the risks of unauthorised access to their data. Of course, this can be done manually, but it requires excellent communication between managers and the IT department. Automated management is far less complex and time-consuming, and it reduces the likelihood of errors.
The phases of the identity life cycle
The Identity Life Cycle phases largely follow the processes of onboarding, transitions and offboarding within an organisation. These terms are often mentioned in the same breath. Below, we provide both a visual and textual representation of the different identity life cycle phases.
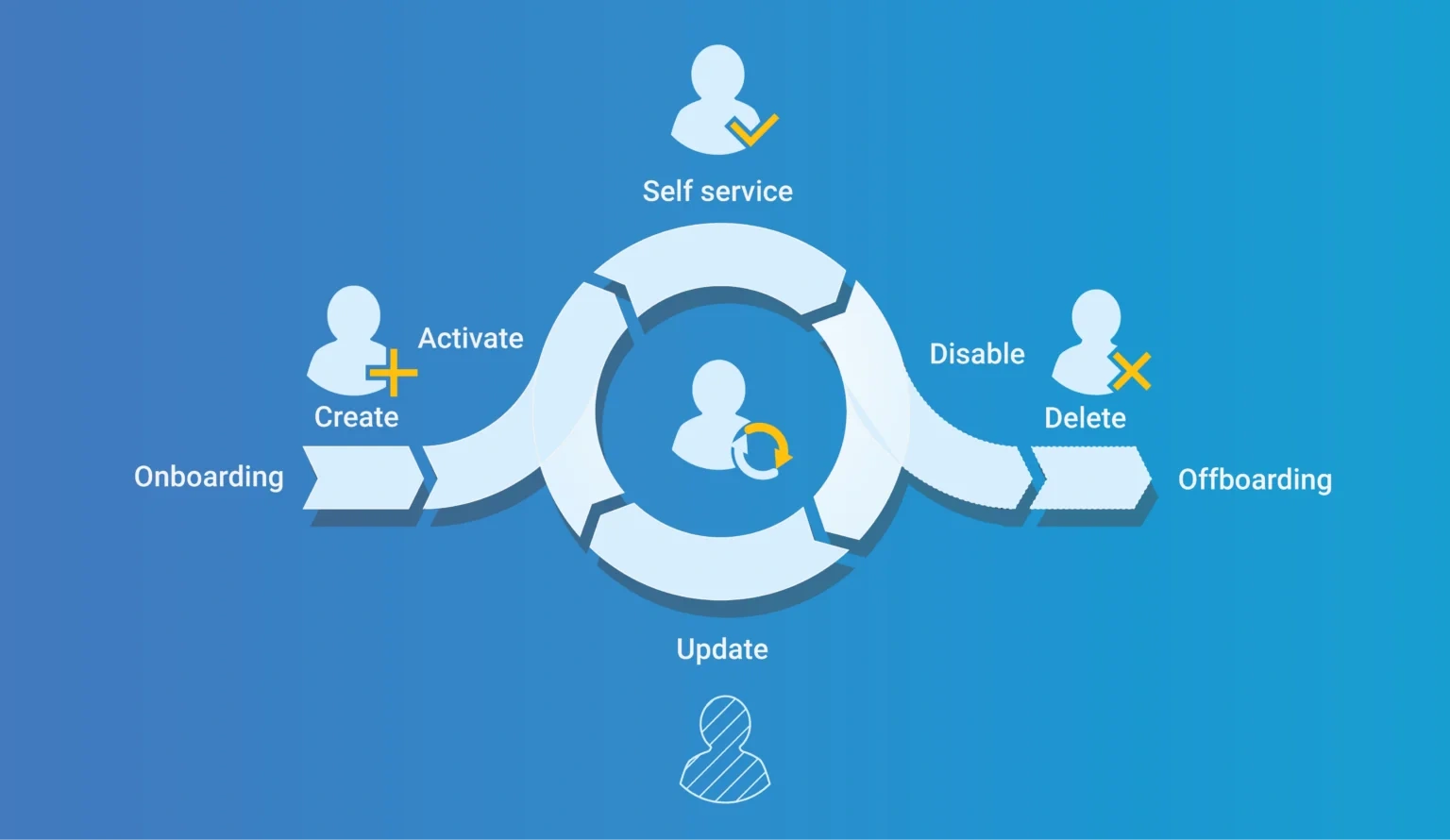
Onboarding
The onboarding phase is the first stage of the identity life cycle. It refers to the process of creating a new identity for a user when they first join an organisation. This stage encompasses two user management tasks: creating an account and activating the account.
When creating an account, basic information about the new employee is collected, such as their name, role and the team they will be joining. This information is then entered into the HRM system by the new manager or by the HR department. Once the employee is fully registered in the HRM system, their data can be accessed by the IAM solution. This is often the moment when the first user account and email address for the individual are created. It usually pertains to a deactivated account, although we increasingly see organisations opting to provide access to the intranet or learning management system even before the start date.
On the day the new employee's contract commences, the accounts are actually activated, and the appropriate permissions and authorisations are granted. This enables the employee to be productive from their very first day.
Transitions
The transition phase is the second stage of the identity life cycle and occurs when an employee undergoes changes in their career or needs. This phase can involve various user management actions:creating, updating and revoking user accounts, and granting and revoking user rights.
During the transition phase, an employee's needs, rights and roles can change, for example, if they change roles, receive a promotion or start using new IT applications. The identity life cycle is not static. Updating and revising user accounts and authorisations are essential to prevent unauthorised access to sensitive or business-critical information and to comply with laws and regulations. In practice, manually updating user accounts and authorisations can be a daunting task for larger organisations. Automated updating and reviewing is a better solution and reduces the risk of errors. An IAM solution can, after each change, validate data against the authorisation matrix to automatically determine what the employee still has access to and to carry out the appropriate actions, such as creating, granting, de-authorising or deactivating accounts or rights.
With self-service and workflow functionality, users can temporarily access specific information or applications without IT intervention. By combining this with automated updating and evaluation of user accounts and authorizations, the transition phase of the identity life cycle can be efficiently and securely managed.
Offboarding
The last stage of the identity life cycle is the offboarding phase. This stage occurs when an employee leaves the organisation. This phase consists of two distinct user management steps: disabling accounts and revoking rights, and deleting/archiving accounts and/or data.
It is crucial to ensure that at the time of leaving the company, all of the employee's user accounts and authorisations are immediately deactivated. This minimises the risk of unauthorised access to sensitive company data. With the link to the HR system, the IAM solution knows when an employee is going to leave the company. This IAM solution deactivates all user accounts on this day and removes the authorisations. This prevents a malicious former employee from potentially stealing sensitive data (consider customer information, intellectual property or account details) or damaging your environment. This way, 'orphaned accounts' are also avoided. Orphaned accounts are accounts no longer linked to an active user but which continue to linger in your IT environment. This 'digital waste' clouds your ability to precisely assess the entirety of current digital identities, access rights and editing rights. But it also consumes unnecessary storage space and licenses.
Depending on the internal rules, not all access necessarily has to be revoked immediately. There are scenarios where you might want to give the employee the chance to securely access their payslips even after their departure date. Over time, user accounts can also be automatically deleted or archived. For such occasions, if the employee re-joins, their account can potentially be reactivated.
How can you optimise the management of the identity life cycle?
An IAM solution like HelloID can assist in optimising the identity life cycle. With it, you can automatically create accounts, assign, update and revoke authorisations, and disable and delete accounts based on a source system like HRM. This not only reduces the chance of errors but also boosts productivity. Employees can get to work faster because the process of creating accounts and assigning authorisations is expedited.
Furthermore, an IAM solution also provides a clear overview of all user accounts, making the management of the identity life cycle simpler. Through reports and dashboards, you can quickly see which user accounts are no longer in use, which user accounts are about to expire, and which user accounts have what access.